#parameterized queries
Explore tagged Tumblr posts
Text
Connecting SQL Statements to C#: Traceability Techniques for Seamless Integration
In the realm of software development, traceability plays a crucial role in ensuring the integrity and maintainability of your codebase. When it comes to connecting SQL statements to C# code, implementing effective traceability techniques becomes even more essential. In this article, we’ll explore practical T-SQL code examples and applications that demonstrate how to establish a robust connection…
View On WordPress
0 notes
Note
For Optimus Prime. What's your favorite things about Ratchet?
[[TRANSMISSION RECEIVED: SUBJECT = QUERY…. SCANNING…. 99% THREAT LEVEL NULL = NO THREAT LEVEL CATAGORIZATION: REROUTING…. SECONDARY SCANS COMPLETE: TRANSMISSION = WITHIN PARAMETERES]]
[[TRANMISSION FORWARDED…. RECEIVED = SEEN]]
[[//RESPONSE IN PROGRESS… RESPONSE COMPLETE: TRANSMISSION SENT//]]
═════════════════
Admittedly this is an unexpected query. I would have thought such a question would be directed toward my host, but I am not opposed to answering. There are many things I find appealing about Ratchet. I could never hope to put a name to all the little pleasantries and habits of his that draw me to him. However if I were to pick out the things that I love most about him, there are only a few traits that I feel fit to be called my 'favorite'.
Firstly there are the purely physical traits of his that catch my optics. I will never find any other as lovely as Ratchet's frame. I do not wish to be... graphic. As such I will simply state that I have always found his sturdy but well sculpted legs to be of great appeal. There is power there that I one day hope to see put to good use outside of his medical duties, perhaps when I am no longer as unsettled by any and all physical interaction. His servos are also a part of him I greatly adore. He has so much strength behind his every action, and yet his movements are calculated and restrained. His touches are light when he is with me and precise when he repairs wounds. When he holds my servo in his, I feel safe and I know that no matter what happens, he will be able to make things right in word or deed. He always has. Of course as much as I adore every other part of him, his optics will always come to my mind alongside that which I have already listed. I am unsure if optics are seen fondly in other courtships, but I love to see Ratchet's whenever I can. Such a deep and very mortal blue hue... I can never get enough of the emotion and the unspoken words behind his every glance. If I could, I would watch for as long as time allows, hoping that the loving blue of his optics could wash away the chill of the white that haunts mine.
As for the other things about him that I could call my favorite? I would have to say his disposition. He is far older than I am, and yet he has the spark of a mech fresh out of training, at least when he wants to showcase his passion. He can love so deeply and put so much of his mind, body, and spark into that which he cares for. It is inspiring to watch him devote his everything to that which he holds dear, including me. I struggle to accept the affection when it is offered, but he is always there to aid me and care for me, helping me when I need it most. He deals with my fear with the patience of Primus himself and always seems to know just what I need even when I do not. Despite all that, he is also capable of projecting his age old wisdom when required. I look up to him when his emotions do not cloud his judgement. He is a mech with so many experiences weighing down his spark, and I cannot help but love him all the more when he takes the lead and shows his skill. He may be a doctor, but when I see him in those moments, the mech that stands before me is a leader Cybertron could have used long before my creation. He has his shortcomings in his wrath and bitterness, but his loyalty and love will always drown those poor qualities out in my mind. I cannot put into words how much I adore him and his devotion. All I can say is that I would give anything to be around him forever, even if only as a phantom just so I could see his spark blaze free and true.
The final aspect of my beloved I can safely say falls into the category of 'favorite' would have to be how he is with our sparkling. One would think that Ratchet matches the textbook descriptor of a Sire right down to the letter. But I beg to differ. I have seen him during the war raising our little warrior, and while outwardly he may appear to act as a Sire, I know Ratchet and what his actions mean. The tender way in which he always held Bumblebee near to his spark chamber, singing a unique song that even I do not know. The manner in which he always methodically tucked Bee into his cradle when he was small, ensuring the mobile above spun at just the correct speed. The methods of which he employed to make sure that Bee's energon was always properly balanced in nutrients. There is so much I could see during those times, so many small things that might have seemed like mere protectiveness or the inclinations of a doctor that really showed his true colors. Ratchet is a Nurturer deep down, and I always adored seeing his gruff yet loving way of showing it. My personal favorite memory of him allowing himself to indulge in his Nurturer coding was shortly after Bumblebee came into our lives. I was doing all I could to care for him with the aid of my host, but we were insufficient when war required my attention. I recall desperately trying to find someone trustworthy to take care of our dear sparkling when Bee began to cry. I could not hear amidst the noise in my workspace, but when I finally came out from the meeting I was engaged in, I found Ratchet there.
He was at the edge of Bumblebee's cradle, singing so gently and with such love that I nearly found myself doubling over in renewed longing. His smile was soft and wistful, belonging to a far younger mech, one untouched by war and blessed with the adoration only a Caretaker could have. Ratchet held out a single digit, allowing Bumblebee to hold it as he dozed off into recharge yet again. It touched my spark, and to this cycle I hold it close to myself. I adore how much Ratchet loves, how much he puts into me, Bumblebee, and the others. The songs he sang to our dozing sparkling, the way he always remained patient with me, and the determination in which he endured my long absence will forever draw me to him, reaffirming my affections.
I want nothing more for Ratchet to be happy. He is such a core part of my life and my past that I do not belief I could ever find it in my spark to be truly angry with him. He was there when no others were, he was dutiful when the rest of the world passed him by, and while I fear for him and the fragility of his mind, I love him more than the world itself. I can never give him everything I want to, my station does not permit it...
But if I were mortal... if I were not confined by the will of the world and the demands of my nature, I would take him away from all of this. I would show him the wonders of the universe and bask him in the passions of my spark. This I would give and so much more.
If I were only mortal.
═════════════════
[[TRANSMISSION SENDER = OPTIMUS PRIME = PRIME OF CYBERTRON: LEADER OF THE AUTOBOTS: PRIMUS’S ANGEL: SAVIOR OF CYBERTRON: LOREKEEPER: SIRE]]
[[TRANSMISSION END]]
#maccadam#transformers#transformers prime au#transformers prime#two sides to a coin au#optimus responds#ratchet#optiratch#optimus prime
35 notes
·
View notes
Text
How to Prevent

Preventing injection requires keeping data separate from commands and queries:
The preferred option is to use a safe API, which avoids using the interpreter entirely, provides a parameterized interface, or migrates to Object Relational Mapping Tools (ORMs). Note: Even when parameterized, stored procedures can still introduce SQL injection if PL/SQL or T-SQL concatenates queries and data or executes hostile data with EXECUTE IMMEDIATE or exec().
Use positive server-side input validation. This is not a complete defense as many applications require special characters, such as text areas or APIs for mobile applications.
For any residual dynamic queries, escape special characters using the specific escape syntax for that interpreter. (escaping technique) Note: SQL structures such as table names, column names, and so on cannot be escaped, and thus user-supplied structure names are dangerous. This is a common issue in report-writing software.
Use LIMIT and other SQL controls within queries to prevent mass disclosure of records in case of SQL injection.
bonus question: think about how query on the image above should look like? answer will be in the comment section
4 notes
·
View notes
Text
SQL Injection in RESTful APIs: Identify and Prevent Vulnerabilities
SQL Injection (SQLi) in RESTful APIs: What You Need to Know
RESTful APIs are crucial for modern applications, enabling seamless communication between systems. However, this convenience comes with risks, one of the most common being SQL Injection (SQLi). In this blog, we’ll explore what SQLi is, its impact on APIs, and how to prevent it, complete with a practical coding example to bolster your understanding.

What Is SQL Injection?
SQL Injection is a cyberattack where an attacker injects malicious SQL statements into input fields, exploiting vulnerabilities in an application's database query execution. When it comes to RESTful APIs, SQLi typically targets endpoints that interact with databases.
How Does SQL Injection Affect RESTful APIs?
RESTful APIs are often exposed to public networks, making them prime targets. Attackers exploit insecure endpoints to:
Access or manipulate sensitive data.
Delete or corrupt databases.
Bypass authentication mechanisms.
Example of a Vulnerable API Endpoint
Consider an API endpoint for retrieving user details based on their ID:
from flask import Flask, request import sqlite3
app = Flask(name)
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = f"SELECT * FROM users WHERE id = {user_id}" # Vulnerable to SQLi cursor.execute(query) result = cursor.fetchone() return {'user': result}, 200
if name == 'main': app.run(debug=True)
Here, the endpoint directly embeds user input (user_id) into the SQL query without validation, making it vulnerable to SQL Injection.
Secure API Endpoint Against SQLi
To prevent SQLi, always use parameterized queries:
@app.route('/user', methods=['GET']) def get_user(): user_id = request.args.get('id') conn = sqlite3.connect('database.db') cursor = conn.cursor() query = "SELECT * FROM users WHERE id = ?" cursor.execute(query, (user_id,)) result = cursor.fetchone() return {'user': result}, 200
In this approach, the user input is sanitized, eliminating the risk of malicious SQL execution.
How Our Free Tool Can Help
Our free Website Security Checker your web application for vulnerabilities, including SQL Injection risks. Below is a screenshot of the tool's homepage:
Upload your website details to receive a comprehensive vulnerability assessment report, as shown below:
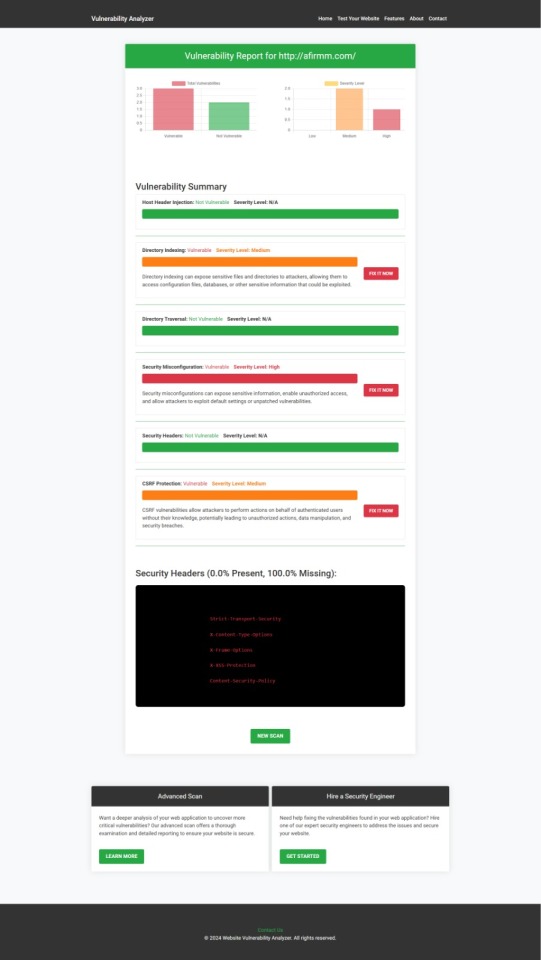
These tools help identify potential weaknesses in your APIs and provide actionable insights to secure your system.
Preventing SQLi in RESTful APIs
Here are some tips to secure your APIs:
Use Prepared Statements: Always parameterize your queries.
Implement Input Validation: Sanitize and validate user input.
Regularly Test Your APIs: Use tools like ours to detect vulnerabilities.
Least Privilege Principle: Restrict database permissions to minimize potential damage.
Final Thoughts
SQL Injection is a pervasive threat, especially in RESTful APIs. By understanding the vulnerabilities and implementing best practices, you can significantly reduce the risks. Leverage tools like our free Website Security Checker to stay ahead of potential threats and secure your systems effectively.
Explore our tool now for a quick Website Security Check.
#cyber security#cybersecurity#data security#pentesting#security#sql#the security breach show#sqlserver#rest api
2 notes
·
View notes
Text
10 security tips for MVC applications in 2023

Model-view-controller or MVC is an architecture for web app development. As one of the most popular architectures of app development frameworks, it ensures multiple advantages to the developers. If you are planning to create an MVC-based web app solution for your business, you must have known about the security features of this architecture from your web development agency. Yes, MVC architecture not only ensures the scalability of applications but also a high level of security. And that’s the reason so many web apps are being developed with this architecture. But, if you are looking for ways to strengthen the security features of your MVC app further, you need to know some useful tips.
To help you in this task, we are sharing our 10 security tips for MVC applications in 2023! Read on till the end and apply these tips easily to ensure high-security measures in your app.
1. SQL Injection: Every business has some confidential data in their app, which needs optimum security measures. SQL Injection is a great threat to security measures as it can steal confidential data through SQL codes. You need to focus on the prevention of SQL injection with parameterized queries, storing encrypted data, inputs validation etc.
2. Version Discloser: Version information can also be dangerous for your business data as it provides hackers with your specific version information. Accordingly, they can attempt to attack your app development version and become successful. Hence, you need to hide the information such as the server, x-powered-by, x-sourcefiles and others.
3. Updated Software: Old, un-updated software can be the reason for a cyber attack. The MVC platforms out there comprise security features that keep on updating. If you also update your MVC platform from time to time, the chances of a cyber attack will be minimized. You can search for the latest security updates at the official sites.
4. Cross-Site Scripting: The authentication information and login credentials of applications are always vulnerable elements that should be protected. Cross-Site Scripting is one of the most dangerous attempts to steal this information. Hence, you need to focus on Cross-Site Scripting prevention through URL encoding, HTML encoding, etc.
5. Strong Authentication: Besides protecting your authentication information, it’s also crucial to ensure a very strong authentication that’s difficult to hack. You need to have a strong password and multi-factor authentication to prevent unauthorized access to your app. You can also plan to hire security expert to ensure strong authentication of your app.
6. Session Management: Another vital security tip for MVA applications is session management. That’s because session-related vulnerabilities are also quite challenging. There are many session management strategies and techniques that you can consider such as secure cookie flags, session expiration, session regeneration etc. to protect access.
7. Cross-Site Request Forgery: It is one of the most common cyber attacks MVC apps are facing these days. When stires process forged data from an untrusted source, it’s known as Cross-Site Request Forgery. Anti-forgery tokens can be really helpful in protecting CSRP and saving your site from the potential danger of data leakage and forgery.
8. XXE (XML External Entity) Attack: XXE attacks are done through malicious XML codes, which can be prevented with the help of DtdProcessing. All you need to do is enable Ignore and Prohibit options in the DtdProcessing property. You can take the help of your web development company to accomplish these tasks as they are the best at it.
9. Role-Based Access Control: Every business has certain roles performed by different professionals, be it in any industry. So, when it comes to giving access to your MVC application, you can provide role-based access. This way, professionals will get relevant information only and all the confidential information will be protected from unauthorized access.
10. Security Testing: Finally, it’s really important to conduct security testing on a regular basis to protect business data on the app from vulnerability. Some techniques like vulnerability scanning and penetration testing can be implied to ensure regular security assessments. It’s crucial to take prompt actions to prevent data leakage and forgery as well.
Since maintaining security should be an ongoing process rather than a one-time action, you need to be really proactive with the above 10 tips. Also, choose a reliable web development consulting agency for a security check of your website or web application. A security expert can implement the best tech stack for better security and high performance on any website or application.
#web development agency#web development consulting#hire security expert#hire web developer#hire web designer#website design company#website development company in usa
2 notes
·
View notes
Text
How to Protect Against SQL Injection Attacks

If you’ve ever built or managed a website that stores user data, you’ve probably heard the term "SQL injection." It’s one of those threats that’s been around for a long time—and it’s still causing real problems. The good news is, with the right habits and checks in place, you can protect your website from falling victim to it.
In this post, we’ll talk about what SQL injection is in simple terms, how it can harm your site, and more importantly, how to prevent it.
What is SQL Injection?
SQL injection is when someone sneaks harmful code into a website’s database query. Think of it like this—your website asks for information from a user (like a login name), and then checks that info in your database. If the website doesn't properly check what's being entered, a hacker could slip in something dangerous that tells the database to give away more than it should—or even delete data altogether.
It’s like leaving your front door open with a sign that says “Come on in.” Not a good idea.
How Can It Affect You?
The biggest risk is your data getting exposed or erased. That could mean user emails, passwords, payment info—anything your website stores. And once that happens, the damage isn’t just technical—it’s also about lost trust. If your visitors feel unsafe, they may never come back.
For small businesses or personal websites, this kind of attack can feel especially overwhelming. That’s why taking steps to prevent it is so important, no matter how big or small your site is.
Tips to Protect Your Site from SQL Injection
Use Prepared Statements (with Parameterized Queries) This is one of the most reliable ways to avoid SQL injection. It simply means your code separates what the user enters from the actual SQL commands. It’s like keeping the guest and the keys to your safe in two different rooms. Most modern programming languages support this method.
Never Trust User Input Always assume that anything a user enters could be harmful. Whether it’s a name, email, or search term—clean it and check it. Don’t just take it and push it straight into your database.
Use Web Application Firewalls (WAF) A firewall helps catch bad requests before they hit your site. Think of it as a filter that looks at incoming traffic and blocks anything that looks suspicious.
Limit Database Permissions Your website doesn’t always need full control over the database. Set up user roles wisely. Even if someone breaks in, they shouldn’t have the power to delete or see everything.
Error Messages Should Be Simple When something goes wrong, don’t show users the technical details. Hackers love to see database errors—they often give away clues about your system. Keep messages general, like “Something went wrong. Please try again.”
Keep Software Updated Whether it's your CMS, plugins, or server software, updates usually include fixes for known problems. Regular updates close the door on old weaknesses.
Validate Input on Both Client and Server Side Check what users are entering on the front end (browser) and also on the back end (server). This double layer keeps things safer.
Use Strong Authentication Don’t let just anyone access your admin panel or database. Use strong passwords, two-factor authentication, and limit login attempts.
The Role of Professional Help
While you can do a lot on your own, sometimes it helps to bring in experts—especially when you're managing sensitive data. That’s why many businesses look to website development companies in Bhubaneswar that specialize in secure coding practices. These companies often have teams who understand how to build safe websites right from the start.
Make Security Part of Your Daily Workflow
Security isn’t a one-time fix. It’s a habit. Just like locking your door every night, your website needs regular checkups and smart routines to stay safe. Train your team, review your code often, and keep learning about new threats. A little attention now can save a lot of stress later.
Final Thoughts
SQL injection attacks are a real threat, but they’re also preventable. With a few smart steps and the right tools, you can keep your site and your users safe. Whether you’re building your own site or working with website development companies in Bhubaneswar, make sure security is part of the plan from the start.
After all, your website is more than just code—it’s a space where people share, buy, learn, and trust. Keeping it secure is one of the best things you can do for your visitors and your business.
#digital marketing agency bhubaneswar#website development companies in bhubaneswar#best digital marketing company in bhubaneswar#digital marketing services in bhubaneswar#web development services in bhubaneswar#digital marketing agency in bhubaneswar
0 notes
Text
B561 Assignment 3
1 Queries with expressions and functions; Boolean queries For the problems in this section, you can use views (including parameterized views, i.e., user-defined functions) but you can not use aggregate functions nor the GROUP BY and HAVING clauses. You can also not use the INNER JOIN (or other joins) operators. 1. Let A(x) and B(x) be two unary relation schemas that represent a set A and a set B,…
0 notes
Text
Securing Your Web Application: Key Strategies for Protection

As the digital landscape continues to evolve, securing web applications has become more important than ever. With the increasing prevalence of cyberattacks, data breaches, and security vulnerabilities, ensuring your web application is protected should be a top priority. Whether you're building a new application or maintaining an existing one, it's critical to take proactive steps to safeguard user data and ensure the security of your platform. For businesses looking to create secure applications, enlisting web application development services can provide the expertise needed to implement the best security practices from the ground up.
Here, we’ll explore some key strategies to help secure your web application and protect it from potential threats.
1. Use HTTPS for Secure Communication
One of the most fundamental steps in securing your web application is ensuring that all communications between users and your servers are encrypted. This is achieved by implementing HTTPS (Hypertext Transfer Protocol Secure). HTTPS uses SSL/TLS certificates to encrypt data, preventing hackers from intercepting sensitive information, such as login credentials, personal data, or payment details.
Without HTTPS, data is transmitted in plain text, making it vulnerable to man-in-the-middle attacks. Make sure that every page of your web application, especially login, registration, and payment pages, uses HTTPS to safeguard your users' information.
2. Implement Strong Authentication and Authorization
Authentication and authorization are essential for verifying user identities and controlling access to your web application’s resources. It’s crucial to implement multi-factor authentication (MFA), which requires users to provide multiple forms of identity verification before granting access.
Additionally, ensure your application follows the principle of least privilege (PoLP) — only allowing users to access resources they absolutely need. This limits the impact of a potential security breach, as even if a hacker gains access to one part of the application, they won’t be able to access all user data or resources.
3. Sanitize Input to Prevent SQL Injection
SQL injection remains one of the most common security vulnerabilities in web applications. This occurs when an attacker manipulates input fields to inject malicious SQL code into your application’s database. To prevent this, always sanitize and validate user input, using parameterized queries and prepared statements when interacting with your database.
Additionally, use input validation libraries and frameworks that automatically escape malicious characters. Never trust user input, and treat all inputs as potentially harmful.
4. Keep Your Software Up to Date
One of the simplest yet most effective ways to secure your web application is by keeping all software up to date. This includes your web application framework, libraries, plugins, and any third-party services you use. Software vendors often release patches and updates to fix security vulnerabilities, so it’s essential to install these updates promptly.
Neglecting to update your software can leave your application open to known exploits that attackers could easily take advantage of. Setting up automated update systems or regularly reviewing available updates can help ensure your application stays secure.
5. Implement Proper Session Management
Session management is another crucial element in securing your web application. Ensure that user sessions are securely managed and expired after a reasonable period of inactivity. Use secure session tokens, which are harder to predict, and store them in a secure location, such as HTTP-only cookies, to reduce the risk of session hijacking.
You should also consider implementing session logging and monitoring to detect unusual activity, such as multiple failed login attempts or sessions accessed from unusual locations. This allows you to act quickly and prevent unauthorized access.
6. Protect Against Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is another common vulnerability in web applications, where attackers inject malicious scripts into web pages viewed by other users. These scripts can steal session cookies, perform actions on behalf of users, or redirect them to malicious websites.
To protect your application from XSS attacks, ensure you sanitize and escape any user-generated content before displaying it. This includes using Content Security Policy (CSP) headers to prevent untrusted scripts from executing and implementing strict input validation to block dangerous scripts.
7. Utilize Web Application Firewalls (WAFs)
A Web Application Firewall (WAF) is a security system that monitors and filters HTTP requests to and from a web application. WAFs can help protect your application from a variety of threats, including SQL injection, XSS, and Distributed Denial of Service (DDoS) attacks.
WAFs work by examining incoming traffic and blocking malicious requests based on predefined security rules. They can also help reduce the risk of zero-day attacks, as they provide an additional layer of protection that may catch unknown vulnerabilities.
8. Regularly Backup Your Data
Even with the best security measures in place, data loss can still happen. Ransomware attacks, hardware failures, and other unforeseen issues can lead to the loss of critical application data. To mitigate this risk, make regular backups of your application data and store them securely.
Test your backups regularly to ensure they can be restored quickly in the event of an attack. Having a solid backup and disaster recovery plan can help you recover your application and minimize downtime in case of a security breach.
9. Conduct Security Audits and Penetration Testing
To ensure that your web application is secure, it’s important to perform regular security audits and penetration testing. A security audit will assess the overall security posture of your application, including code reviews, infrastructure assessments, and configuration checks.
Penetration testing, or ethical hacking, involves simulating an attack to identify vulnerabilities before malicious hackers can exploit them. By conducting these tests regularly, you can identify weaknesses and patch them before they become a problem.
Conclusion
Securing your web application is an ongoing process that requires vigilance, expertise, and the adoption of best practices. By implementing strong authentication, keeping software up to date, sanitizing input, and using tools like WAFs and encryption, you can protect your application from a variety of threats and ensure a safe experience for your users.
If you're looking to create a secure and robust web application, partnering with a web application development company can help ensure that security is embedded into your application from the start. Their expertise in building secure, scalable solutions can help you avoid common pitfalls and provide the protection your users expect.
0 notes
Text
Enhancing Security in Backend Development: Best Practices for Developers
In today’s rapidly evolving digital environment, security in backend systems is paramount. As the backbone of web applications, the backend handles sensitive data processing, storage, and communication. Any vulnerabilities in this layer can lead to catastrophic breaches, affecting user trust and business integrity. This article highlights essential best practices to ensure your backend development meets the highest security standards.
1. Implement Strong Authentication and Authorization
One of the primary steps in securing backend development services is implementing robust authentication and authorization protocols. Password-based systems alone are no longer sufficient. Modern solutions like OAuth 2.0 and JSON Web Tokens (JWT) offer secure ways to manage user sessions. Multi-factor authentication (MFA) adds another layer of protection, requiring users to verify their identity using multiple methods, such as a password and a one-time code.
Authorization should be handled carefully to ensure users only access resources relevant to their role. By limiting privileges, you reduce the risk of sensitive data falling into the wrong hands. This practice is particularly crucial for applications that involve multiple user roles, such as administrators, managers, and end-users.
2. Encrypt Data in Transit and at Rest
Data encryption is a non-negotiable aspect of backend security. When data travels between servers and clients, it is vulnerable to interception. Implement HTTPS to secure this communication channel using SSL/TLS protocols. For data stored in databases, use encryption techniques that prevent unauthorized access. Even if an attacker gains access to the storage, encrypted data remains unreadable without the decryption keys.
Managing encryption keys securely is equally important. Store keys in hardware security modules (HSMs) or use services like AWS Key Management Service (KMS) to ensure they are well-protected. Regularly rotate keys to further reduce the risk of exposure.
3. Prevent SQL Injection and Other Injection Attacks
Injection attacks, particularly SQL injections, remain one of the most common threats to backend technologies for web development. Attackers exploit poorly sanitized input fields to execute malicious SQL queries. This can lead to unauthorized data access or even complete control of the database.
To mitigate this risk, always validate and sanitize user inputs. Use parameterized queries or prepared statements, which ensure that user-provided data cannot alter the intended database commands. Additionally, educate developers on the risks of injection attacks and implement static code analysis tools to identify vulnerabilities during the development process.
4. Employ Secure API Design
APIs are integral to backend development but can also serve as entry points for attackers if not secured properly. Authentication tokens, input validation, and rate limiting are essential to preventing unauthorized access and abuse. Moreover, all API endpoints should be designed with security-first principles.
For example, avoid exposing sensitive information in API responses. Error messages should be generic and not reveal the backend structure. Consider using tools like API gateways to enforce security policies, including data masking, IP whitelisting, and token validation.
5. Keep Dependencies Updated and Patched
Third-party libraries and frameworks streamline development but can introduce vulnerabilities if not updated regularly. Outdated software components are a common attack vector. Perform routine dependency checks and integrate automated vulnerability scanners like Snyk or Dependabot into your CI/CD pipeline.
Beyond updates, consider using tools to analyze your application for known vulnerabilities. For instance, dependency management tools can identify and notify you of outdated libraries, helping you stay ahead of potential risks.
6. Adopt Role-Based Access Control (RBAC)
Access management is a critical component of secure backend systems. Role-Based Access Control (RBAC) ensures users and applications have access only to what they need. Define roles clearly and assign permissions at a granular level. For example, a customer service representative may only access user profile data, while an admin might have permissions to modify backend configurations.
Implementing RBAC reduces the potential damage of a compromised user account. For added security, monitor access logs for unusual patterns, such as repeated failed login attempts or unauthorized access to restricted resources.
7. Harden Your Database Configurations
Databases are at the heart of backend systems, making them a prime target for attackers. Properly configuring your database is essential. Start by disabling unnecessary services and default accounts that could be exploited. Enforce strong password policies and ensure that sensitive data, such as passwords, is hashed using secure algorithms like bcrypt or Argon2.
Database permissions should also be restricted. Grant the least privilege necessary to applications interacting with the database. Regularly audit these permissions to identify and eliminate unnecessary access.
8. Monitor and Log Backend Activities
Real-time monitoring and logging are critical for detecting and responding to security threats. Implement tools like Logstash, Prometheus, and Kibana to track server activity and identify anomalies. Logs should include information about authentication attempts, database queries, and API usage.
However, ensure that logs themselves are secure. Store them in centralized, access-controlled environments and avoid exposing them to unauthorized users. Use log analysis tools to proactively identify patterns that may indicate an ongoing attack.
9. Mitigate Cross-Site Scripting (XSS) Risks
Cross-site scripting attacks can compromise your backend security through malicious scripts. To prevent XSS attacks, validate and sanitize all inputs received from the client side. Implement Content Security Policies (CSP) that restrict the types of scripts that can run within the application.
Another effective measure is to encode output data before rendering it in the user’s browser. For example, HTML encoding ensures that malicious scripts cannot execute, even if injected.
10. Secure Cloud Infrastructure
As businesses increasingly migrate to the cloud, backend developers must adapt to the unique challenges of cloud security. Use Identity and Access Management (IAM) features provided by cloud platforms like AWS, Google Cloud, and Azure to define precise permissions.
Enable encryption for all data stored in the cloud and use virtual private clouds (VPCs) to isolate your infrastructure from external threats. Regularly audit your cloud configuration to ensure compliance with security best practices.
11. Foster a Culture of Security
Security isn’t a one-time implementation — it’s an ongoing process. Regularly train your development team on emerging threats, secure coding practices, and compliance standards. Encourage developers to follow a security-first approach at every stage of development.
Conduct routine penetration tests and code audits to identify weaknesses. Establish a response plan to quickly address breaches or vulnerabilities. By fostering a security-conscious culture, your organization can stay ahead of evolving threats.
Thus, Backend security is an ongoing effort requiring vigilance, strategic planning, and adherence to best practices. Whether you’re managing APIs, databases, or cloud integrations, securing backend development services ensures the reliability and safety of your application.
0 notes
Note
For optimus and ratchet; how often do you think about kissing?
[[TRANSMISSION RECEIVED: SUBJECT = QUERY…. SCANNING…. 99% THREAT LEVEL NULL = NO THREAT LEVEL CATAGORIZATION: REROUTING…. SECONDARY SCANS COMPLETE: TRANSMISSION = WITHIN PARAMETERES]]
[[TRANMISSION FORWARDED…. RECEIVED = SEEN]]
[[//RESPONSE IN PROGRESS… RESPONSE COMPLETE: TRANSMISSION SENT//]]
═════════════════
I am... not the most comfortable answering this query. However I will state rather simply that I consider it far more often than I likely should be. It is not fitting for a Prime, not when my world still remains largely in ruins and its people fighting for order. Yet I cannot help but find my beloved alluring at inopportune times.
I am aware he is one of the oldest functioning mecha on Cybertron, and thus his frame is neither youthful or particularly in line with current trends. Despite that, I adore him. There is nothing about him I could ever find in my spark to despise. I almost always want to lean down to press kisses to his face and jaw when I see him in the halls. When he is stressed I constantly wish to touch every crease and exposed seam to ease him, especially when he is at his desk and trying to drink his concerns into oblivion. I want to bask him in my affection and smother his worries with my love. I would give anything to hold him in my arms during council meetings and kiss him until it all fades away. But of course, that is not acceptable, and it never will be.
It is most difficult to keep my mind away from his alluring derma when I am dealing with paperwork. It is an impossible task to perform such mind numbing work and not think about far more pleasant things. More than once I have found myself... warmer than I should be when left for cycles at a time to my own devices. I crave Ratchet's affection and his touch, and yet it is not mine to have... not now, not while I am still needed. Until times change, I can only give him a small portion of what my spark longs to offer.
I will forward your query to Ratchet so that he may answer as well should he feel so inclined.
═════════════════
[[TRANSMISSION SENDER = OPTIMUS PRIME = PRIME OF CYBERTRON: LEADER OF THE AUTOBOTS: PRIMUS’S ANGEL: SAVIOR OF CYBERTRON: LOREKEEPER: SIRE]]
[[RESPONSE ENCRYPTED: ANCIENT SCRIPT IDENTIFIED: QUERY FORWARDED... RECEIVED... SEEN]]
[[//RESPONSE IN PROGRESS… RESPONSE COMPLETE: TRANSMISSION SENT//]]
═════════════════
You are rather nosy aren't you anonymous? Evidently Optimus thinks so too considering his response has been encrypted. However since he has forwarded me your not at all subtle prod at our personal lives, I assume Optimus would like for me to answer.
Very well, here is your answer.
If I am totally honest, I think about him whenever I am not occupied with anything more pressing. He is the most gorgeous mech I have ever laid optics on. The only runner up I can think of would have to be Deadlock. That mech was a piece of work, but he had quite a few of the traits I find so appealing in Optimus. Quite frankly I have not gone one cycle without thinking about kissing Optimus. He deserves it and it gets him out of his processors. Not to mention he is surprisingly good at it despite having no real experience. There is something electric about kissing him. Can you blame me for wanting to seek that feeling out more?
He's so uncertain when I finally get a moment to snag a kiss from him, but I can tell he enjoys it too. Our little moments are wonderful and I only wish they could come more often. It is almost impossible to not march over and kiss him when he is in his full primal garb. I don't think Optimus has ever looked more stunning than when the Chaplains and their assistants get him looking like a true demi-god. So far I have only gotten one kiss out of him when he is dressed up, but that was by far one of the best. Optimus is more confident when he is adorned fittingly for his station, not to mention Paradox always applies a little bit of tinted shiner to Optimus's derma when he gets my Prime ready. I don't know if he does it just to make Optimus more appealing or to bother me, but whatever the case, I thank him for it.
If I had the power I would steal Optimus away and kiss him until I am physically unable. But as Optimus loves to say "duty comes first". Slagging duty...
I hope that answers your query.
═════════════════
[[TRANSMISSION SENDER = RATCHET OF IACON = PRIMAL STEWARD: CHIEF MEDICAL OFFICER: WAR VETERAN: HONORARY MILITARY OFFICAL: NURTURER]]
[[TRANSMISSION ENDS]]
#maccadam#transformers prime au#transformers#transformers prime#two sides to a coin au#optiratch#optimus prime#optimus responds#ratchet responds#ratchet
27 notes
·
View notes
Text
SQLi Potential Mitigation Measures
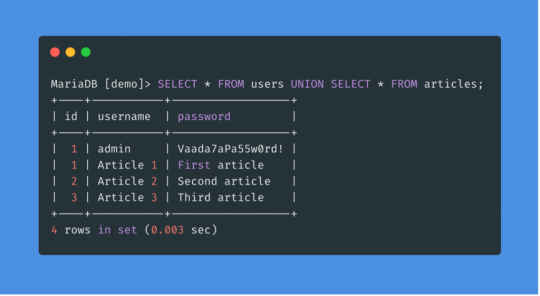
Phase: Architecture and Design
Strategy: Libraries or Frameworks
Use a vetted library or framework that prevents this weakness or makes it easier to avoid. For example, persistence layers like Hibernate or Enterprise Java Beans can offer protection against SQL injection when used correctly.
Phase: Architecture and Design
Strategy: Parameterization
Use structured mechanisms that enforce separation between data and code, such as prepared statements, parameterized queries, or stored procedures. Avoid constructing and executing query strings with "exec" to prevent SQL injection [REF-867].
Phases: Architecture and Design; Operation
Strategy: Environment Hardening
Run your code with the minimum privileges necessary for the task [REF-76]. Limit user privileges to prevent unauthorized access if an attack occurs, such as by ensuring database applications don’t run as an administrator.
Phase: Architecture and Design
Duplicate client-side security checks on the server to avoid CWE-602. Attackers can bypass client checks by altering values or removing checks entirely, making server-side validation essential.
Phase: Implementation
Strategy: Output Encoding
Avoid dynamically generating query strings, code, or commands that mix control and data. If unavoidable, use strict allowlists, escape/filter characters, and quote arguments to mitigate risks like SQL injection (CWE-88).
Phase: Implementation
Strategy: Input Validation
Assume all input is malicious. Use strict input validation with allowlists for specifications and reject non-conforming inputs. For SQL queries, limit characters based on parameter expectations for attack prevention.
Phase: Architecture and Design
Strategy: Enforcement by Conversion
For limited sets of acceptable inputs, map fixed values like numeric IDs to filenames or URLs, rejecting anything outside the known set.
Phase: Implementation
Ensure error messages reveal only necessary details, avoiding cryptic language or excessive information. Store sensitive error details in logs but be cautious with content visible to users to prevent revealing internal states.
Phase: Operation
Strategy: Firewall
Use an application firewall to detect attacks against weaknesses in cases where the code can’t be fixed. Firewalls offer defense in depth, though they may require customization and won’t cover all input vectors.
Phases: Operation; Implementation
Strategy: Environment Hardening
In PHP, avoid using register_globals to prevent weaknesses like CWE-95 and CWE-621. Avoid emulating this feature to reduce risks. source
3 notes
·
View notes
Text
What is HarmonyOS NEXT - RelationalStore?
Relational databases provide a universal operational interface for applications, with SQLite as the persistent storage engine at the underlying level, supporting the database features of SQLite, including but not limited to transactions, indexes, views, triggers, foreign keys, parameterized queries, and precompiled SQL statements.
Applicable scenarios: In scenarios where complex relational data is stored, such as the student information of a class, which needs to include names, student IDs, subject grades, etc., or the employee information of a company, which needs to include names, job IDs, positions, etc. Due to the strong correspondence between data, the complexity is higher than that of key value data. In this case, a relational database needs to be used to persistently store the data.
constraint qualification ·The default logging mode of the system is WAL (Write Ahead Log) mode, and the default disk dropping mode is FULL mode. ·There are 4 read connections and 1 write connection in the database. When a thread obtains a free read connection, it can perform a read operation. When there is no free read connection and there is a free write connection, the write connection will be used as a read connection. ·To ensure data accuracy, the database can only support one write operation at a time. ·After the application is uninstalled, the relevant database files and temporary files on the device will be automatically cleared. ·Basic data types supported by ArkTS side: number、string、 Binary type data boolean。 ·To ensure successful insertion and reading of data, it is recommended that one piece of data should not exceed 2M. Exceeding this size, insertion successful, read failed.
Basic concepts: ·Predicate: A term used in a database to represent the properties, characteristics, or relationships between data entities, primarily used to define the operating conditions of the database. ·Result set: refers to the set of results obtained by the user after querying, which can be accessed for data. The result set provides a flexible way of accessing data, making it easier for users to obtain the data they want.
code example SQLiteUtil [code] export default class SQLiteUtil { static getCreateTableSql(tableName: string, columns: ColumnInfo[]): string { let sql = CREATE TABLE IF NOT EXISTS ${tableName} (; columns.forEach((element, index) => { if (index == 0) { //Splicing the first element, default as primary key sql += ${element.name} ${DataType[element.type]} PRIMARY KEY AUTOINCREMENT,; } else if (index == columns.length - 1) { //Last element concatenation statement sql += ${element.name} ${DataType[element.type]} NOT NULL);; } else { sql += ${element.name} ${DataType[element.type]} NOT NULL,; } }); return sql; } }
export interface ColumnInfo { name: string; type: DataType; }
export enum DataType { NULL = 'NULL', INTEGER = 'INTEGER', REAL = 'REAL', TEXT = 'TEXT', BLOB = 'BLOB' } [/code] RelationalStoreService [code] import SQLiteUtil, { ColumnInfo, DataType } from '../ChicKit/data/SQLiteUtil' import relationalStore from '@ohos.data.relationalStore' import { common } from '@kit.AbilityKit'; import Logger from '../utils/Logger'; import AppError from '../models/AppError'; import Schedule from '../entities/Schedule'; import { BusinessError } from '@kit.BasicServicesKit'; import { ValuesBucket, ValueType } from '@ohos.data.ValuesBucket'; import { DataModel } from '../ChicKit/data/DataModel'; import Target from '../entities/Target'; import Plan from '../entities/Plan';
const RelationalStoreName = 'shijianxu.db'
export default class RelationalStoreService { static rdbStore: relationalStore.RdbStore;
/**
Initialize relational database
@param context */ static init(context: common.UIAbilityContext) { // RelationalStore configuration let storeConfig: relationalStore.StoreConfig = { // Database file name name: RelationalStoreName, //security level securityLevel: relationalStore.SecurityLevel.S1 } relationalStore.getRdbStore(context, storeConfig, (err, store) => { if (err) { Logger.error(RelationalStoreService init error, error=${JSON.stringify(new AppError(err))}) return; } else { RelationalStoreService.rdbStore = store RelationalStoreService.createScheduleTable() RelationalStoreService.createTargetTable() RelationalStoreService.createPlanTable() } }); } /**
Create schedule table */ static createScheduleTable() { //Table Fields const columns: ColumnInfo[] = Schedule.getColumns() // Retrieve the SQL statement for creating a table const sql = SQLiteUtil.getCreateTableSql(Schedule.TableName, columns) // Create Data Table RelationalStoreService.rdbStore.executeSql(sql, (err) => { if (err) { Logger.error(RelationalStoreService createScheduleTable error, error=${JSON.stringify(new AppError(err))}) return; } }); } /**
Create target table */ static createTargetTable() { //表字段 const columns: ColumnInfo[] = Target.getColumns() // 获取创建表SQL语句 const sql = SQLiteUtil.getCreateTableSql(Target.TableName, columns) // 创建数据表 RelationalStoreService.rdbStore.executeSql(sql, (err) => { if (err) { Logger.error(RelationalStoreService createTargetTable error, error=${JSON.stringify(new AppError(err))}) return; } }); } /**
Create plan table */ static createPlanTable() { //表字段 const columns: ColumnInfo[] = Plan.getColumns() // 获取创建表SQL语句 const sql = SQLiteUtil.getCreateTableSql(Plan.TableName, columns) // 创建数据表 RelationalStoreService.rdbStore.executeSql(sql, (err) => { if (err) { Logger.error(RelationalStoreService createPlanTable error, error=${JSON.stringify(new AppError(err))}) return; } }); } /**
insert data
@param tableName
@param values */ static insert(tableName: string, values: ValuesBucket) { RelationalStoreService.rdbStore.insert(tableName, values, (err: BusinessError, rowId: number) => { if (err) { Logger.error(RelationalStoreService insert error, error=${JSON.stringify(new AppError(err))}) return; } else { return rowId } }) } /**
delete
@param predicates
@returns delete count */ static delete(predicates: relationalStore.RdbPredicates):number{ return RelationalStoreService.rdbStore.deleteSync(predicates) } /**
update
@param values
@param predicates
@returns update count */ static update(values: ValuesBucket,predicates: relationalStore.RdbPredicates):number{ let rows: number = RelationalStoreService.rdbStore.updateSync(values, predicates, relationalStore.ConflictResolution.ON_CONFLICT_REPLACE); return rows } static querySync(predicates: relationalStore.RdbPredicates, columns: ColumnInfo[]): DataModel[] { let dataList: DataModel[] = [] try { let columnsStringArray: string[] = [] columns.forEach(element => { columnsStringArray.push(element.name) }); const resultSet = RelationalStoreService.rdbStore.querySync(predicates, columnsStringArray) resultSet.columnNames // resultSet.getColumnName('') // resultSet.getValue() //循环处理结果,循环条件:当所在行不是最后一行 while (!resultSet.isAtLastRow) { //去往下一行 resultSet.goToNextRow() let schedule: DataModel = {} columns.forEach(element => { switch (element.type) { case DataType.INTEGER: schedule[element.name] = resultSet.getLong(resultSet.getColumnIndex(element.name)) break; case DataType.REAL: schedule[element.name] = resultSet.getDouble(resultSet.getColumnIndex(element.name)) break; case DataType.TEXT: schedule[element.name] = resultSet.getString(resultSet.getColumnIndex(element.name)) break; case DataType.BLOB: schedule[element.name] = resultSet.getBlob(resultSet.getColumnIndex(element.name)) break; } }) dataList.push(schedule) } } catch (err) { Logger.error(RelationalStoreService querySync error, error=${JSON.stringify(new AppError(err))}) } return dataList } } [/code]
0 notes
Text
Innovations in Data Orchestration: How Azure Data Factory is Adapting

Introduction
As businesses generate and process vast amounts of data, the need for efficient data orchestration has never been greater. Data orchestration involves automating, scheduling, and managing data workflows across multiple sources, including on-premises, cloud, and third-party services.
Azure Data Factory (ADF) has been a leader in ETL (Extract, Transform, Load) and data movement, and it continues to evolve with new innovations to enhance scalability, automation, security, and AI-driven optimizations.
In this blog, we will explore how Azure Data Factory is adapting to modern data orchestration challenges and the latest features that make it more powerful than ever.
1. The Evolution of Data Orchestration
🚀 Traditional Challenges
Manual data integration between multiple sources
Scalability issues in handling large data volumes
Latency in data movement for real-time analytics
Security concerns in hybrid and multi-cloud setups
🔥 The New Age of Orchestration
With advancements in cloud computing, AI, and automation, modern data orchestration solutions like ADF now provide: ✅ Serverless architecture for scalability ✅ AI-powered optimizations for faster data pipelines ✅ Real-time and event-driven data processing ✅ Hybrid and multi-cloud connectivity
2. Key Innovations in Azure Data Factory
✅ 1. Metadata-Driven Pipelines for Dynamic Workflows
ADF now supports metadata-driven data pipelines, allowing organizations to:
Automate data pipeline execution based on dynamic configurations
Reduce redundancy by using parameterized pipelines
Improve reusability and maintenance of workflows
✅ 2. AI-Powered Performance Optimization
Microsoft has introduced AI-powered recommendations in ADF to:
Suggest best data pipeline configurations
Automatically optimize execution performance
Detect bottlenecks and improve parallelism
✅ 3. Low-Code and No-Code Data Transformations
Mapping Data Flows provide a visual drag-and-drop interface
Wrangling Data Flows allow users to clean data using Power Query
Built-in connectors eliminate the need for custom scripting
✅ 4. Real-Time & Event-Driven Processing
ADF now integrates with Event Grid, Azure Functions, and Streaming Analytics, enabling:
Real-time data movement from IoT devices and logs
Trigger-based workflows for automated data processing
Streaming data ingestion into Azure Synapse, Data Lake, or Cosmos DB
✅ 5. Hybrid and Multi-Cloud Data Integration
ADF now provides:
Expanded connector support (AWS S3, Google BigQuery, SAP, Databricks)
Enhanced Self-Hosted Integration Runtime for secure on-prem connectivity
Cross-cloud data movement with Azure, AWS, and Google Cloud
✅ 6. Enhanced Security & Compliance Features
Private Link support for secure data transfers
Azure Key Vault integration for credential management
Role-based access control (RBAC) for governance
✅ 7. Auto-Scaling & Cost Optimization Features
Auto-scaling compute resources based on workload
Cost analysis tools for optimizing pipeline execution
Pay-per-use model to reduce costs for infrequent workloads
3. Use Cases of Azure Data Factory in Modern Data Orchestration
🔹 1. Real-Time Analytics with Azure Synapse
Ingesting IoT and log data into Azure Synapse
Using event-based triggers for automated pipeline execution
🔹 2. Automating Data Pipelines for AI & ML
Integrating ADF with Azure Machine Learning
Scheduling ML model retraining with fresh data
🔹 3. Data Governance & Compliance in Financial Services
Secure movement of sensitive data with encryption
Using ADF with Azure Purview for data lineage tracking
🔹 4. Hybrid Cloud Data Synchronization
Moving data from on-prem SAP, SQL Server, and Oracle to Azure Data Lake
Synchronizing multi-cloud data between AWS S3 and Azure Blob Storage
4. Best Practices for Using Azure Data Factory in Data Orchestration
✅ Leverage Metadata-Driven Pipelines for dynamic execution ✅ Enable Auto-Scaling for better cost and performance efficiency ✅ Use Event-Driven Processing for real-time workflows ✅ Monitor & Optimize Pipelines using Azure Monitor & Log Analytics ✅ Secure Data Transfers with Private Endpoints & Key Vault
5. Conclusion
Azure Data Factory continues to evolve with innovations in AI, automation, real-time processing, and hybrid cloud support. By adopting these modern orchestration capabilities, businesses can:
Reduce manual efforts in data integration
Improve data pipeline performance and reliability
Enable real-time insights and decision-making
As data volumes grow and cloud adoption increases, Azure Data Factory’s future-ready approach ensures that enterprises stay ahead in the data-driven world.
WEBSITE: https://www.ficusoft.in/azure-data-factory-training-in-chennai/
0 notes
Text
How Symfony Software Development Enhances Web Performance and Security?

In today’s digital era, businesses need web applications that are not only feature-rich but also high-performing and secure. Symfony, a leading PHP framework, has become a preferred choice for web application development due to its robust architecture, performance optimization features, and advanced security mechanisms. Let’s explore how Symfony software development enhances web performance and security.
Performance Optimization with Symfony
1. Efficient Caching Mechanism
Symfony’s built-in caching system ensures that web applications load faster and use fewer server resources. It supports multiple caching methods such as HTTP caching, application caching, and OPcache integration, reducing redundant computations and improving response times.
2. Code Reusability and Modularity
Symfony is designed around reusable components and a modular architecture. This reduces the need for redundant code, making the application lightweight and improving execution speed. Developers can integrate only the necessary components, ensuring optimized performance.
3. Autoloading and Dependency Injection
Symfony uses an efficient autoloading system that eliminates the need to manually include files. Additionally, its powerful dependency injection container reduces memory consumption, allowing applications to run faster with fewer resources.
4. Database Optimization
Symfony’s Doctrine ORM (Object-Relational Mapping) optimizes database queries by reducing unnecessary calls and enabling query caching. This ensures faster data retrieval and better database performance.
5. Built-in Debugging and Profiling Tools
Symfony’s debugging tools, such as the Web Debug Toolbar and Profiler, help developers identify performance bottlenecks. By optimizing slow queries and refining application logic, Symfony ensures enhanced application speed and efficiency.
Enhancing Security with Symfony
1. Secure Authentication and Authorization
Symfony offers a built-in security system that provides robust authentication and authorization mechanisms. It supports multi-factor authentication, OAuth, JWT, and LDAP integrations, ensuring secure user access and preventing unauthorized logins.
2. Protection Against Common Web Threats
Symfony is designed to protect applications from common security threats, including:
Cross-Site Scripting (XSS): It automatically escapes output to prevent malicious script injections.
Cross-Site Request Forgery (CSRF): Symfony includes built-in CSRF protection to safeguard forms from unauthorized requests.
SQL Injection Prevention: By using Doctrine ORM, Symfony prevents direct SQL injections by implementing parameterized queries.
3. Secure Data Encryption
Symfony supports data encryption mechanisms such as bcrypt and Argon2 hashing for password storage. It also enables secure transmission of sensitive data using SSL/TLS protocols.
4. Regular Security Updates and Community Support
Symfony has an active community and a dedicated security team that continuously monitors vulnerabilities and releases regular updates and patches. This ensures applications remain secure against evolving cyber threats.
Conclusion
Symfony software development is an excellent choice for businesses looking to build high-performing and secure web applications. With its powerful caching mechanisms, optimized database queries, and security-focused architecture, Symfony ensures enhanced web performance and protection against cyber threats. By leveraging Symfony’s capabilities, businesses can deliver fast, scalable, and secure web applications, ensuring a seamless user experience.
0 notes
Text
How to Prevent NoSQL Injection in Laravel Apps: A Step-by-Step Guide
Introduction
In modern web development, NoSQL databases like MongoDB offer flexibility and scalability. However, they also introduce unique security challenges, one of the most critical being NoSQL injection attacks.

This article explores how these attacks can affect Laravel applications and provides practical coding examples to help prevent them.
What Is NoSQL Injection?
NoSQL injection is a type of attack where an attacker manipulates queries sent to a NoSQL database to access or modify unauthorized data. Unlike traditional SQL injection, NoSQL injection exploits the query language and structure of NoSQL databases.
How NoSQL Injection Affects Laravel Applications
Laravel is a popular PHP framework that supports multiple database types, including NoSQL databases like MongoDB through extensions. Unfortunately, if developers use unsanitized user input in their queries, it opens the door for potential injection attacks.
Example Scenario: Vulnerable Login Function
Consider a Laravel application using MongoDB to authenticate users. A typical login function might look like this:
public function login(Request $request) { $user = User::where('email', $request->email) ->where('password', $request->password) ->first(); if ($user) { // User authenticated } else { // Authentication failed } }
In this example, if $request->email or $request->password contains malicious input, the query can be manipulated, potentially allowing an attacker to bypass authentication.
Preventing NoSQL Injection in Laravel
1. Input Validation and Sanitization
To prevent NoSQL injection, always validate and sanitize user inputs to ensure they follow the expected format. Laravel provides built-in validation methods to handle this effectively.
$validated = $request->validate([ 'email' => 'required|email', 'password' => 'required|string|min:8', ]);
2. Use Parameterized Queries
Avoid embedding user inputs directly into queries. Instead, use parameterized queries or Laravel's query builder, which automatically handles input sanitization.
$user = User::where('email', $validated['email']) ->where('password', $validated['password']) ->first();
3. Implement Secure Authentication
Rather than comparing plain-text passwords, use Laravel's built-in authentication features that hash passwords securely and offer robust authentication mechanisms.
if (Auth::attempt(['email' => $validated['email'], 'password' => $validated['password']])) { // User authenticated } else { // Authentication failed }
Visual Demonstration
Here are two helpful images to showcase the security features and effectiveness of testing tools:
1. Screenshot of the Free Website Security Scanner Tool
Screenshot of the free tools webpage where you can access security assessment tools.
2. Screenshot of a Website Vulnerability Assessment Report
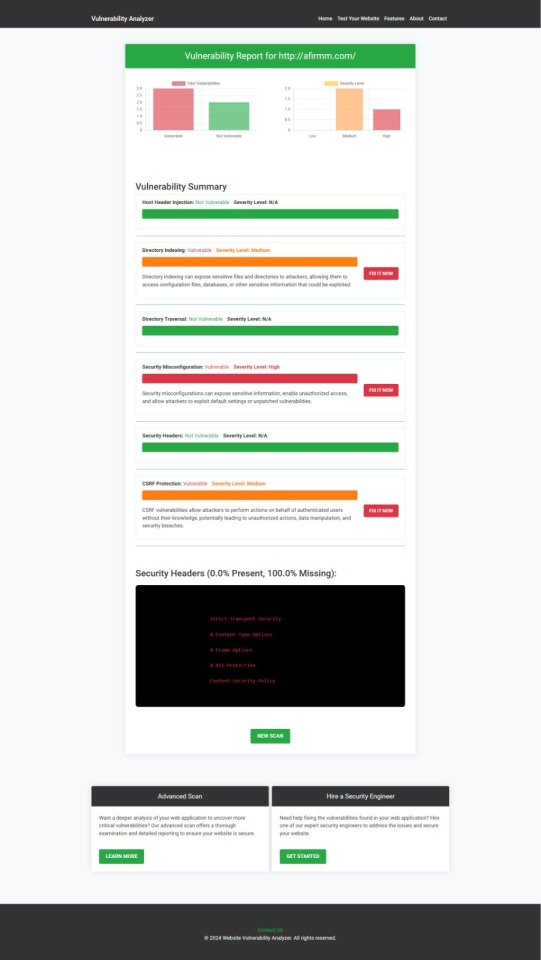
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
NoSQL injection attacks can pose significant threats to web applications, including those built with Laravel. However, by following best practices such as input validation, using parameterized queries, and leveraging Laravel's authentication features, you can significantly reduce the risk of these attacks.
Regularly testing your website with tools like ours to check website vulnerability can further enhance your application's security posture.
For more insights on web application security, visit the Pentest Testing Corp Blog.
1 note
·
View note
Text
Azure Data Engineering Certification | Azure Data Engineer
How to Monitor and Debug Pipelines in Azure Data Factory?
Azure Data Factory (ADF) is a comprehensive, cloud-based data integration service that enables the creation, scheduling, and orchestration of data pipelines. Efficient monitoring and debugging of pipelines are essential for ensuring seamless data flows and swift problem resolution. In this article, we explore the tools and methods for monitoring and debugging pipelines in Azure Data Factory. Microsoft Azure Data Engineer

Monitoring Pipelines in Azure Data Factory
Monitoring is crucial for detecting issues early, ensuring data accuracy, and maintaining pipeline performance. Azure Data Factory offers various tools to help with this task:
Azure Monitor Integration
Azure Monitor provides a unified platform to track and analyze pipeline activities. It offers capabilities such as:
Tracking pipeline, activity, and trigger runs.
Setting alerts for failures, long runtimes, or specific conditions.
Using log analytics to query detailed pipeline logs and gain insights into pipeline performance. Azure Data Engineer Course
Monitoring via ADF Portal
The ADF portal provides several views for monitoring pipeline activity:
Pipeline Runs View: Displays a summary of all pipeline runs, including their status (e.g., Succeeded, Failed), start time, and duration.
Activity Runs View: Provides visibility into the execution of individual activities within a pipeline.
Trigger Runs View: Tracks the execution of schedule- or event-based triggers and their associated pipelines.
Alerts and Notifications
Using Azure Monitor, you can configure alerts for pipeline failures or other critical issues. Alerts can be sent through email, SMS, or other channels, allowing quick intervention when necessary.
Integration with Application Insights
Application Insights enables advanced telemetry tracking for your pipelines, including custom metrics and tracing. This integration is particularly beneficial when you need detailed insights into the pipeline's execution, beyond the basic metrics.
Debugging Pipelines in Azure Data Factory
Efficient debugging is vital for identifying and resolving errors during pipeline development and execution. ADF provides a range of tools to assist in this process: Azure Data Engineer Course Online
Debug Mode
ADF’s Debug mode allows you to test your pipeline's execution before publishing changes:
Run individual activities or full pipeline executions.
View detailed outputs and error messages for each activity.
Test parameterized pipelines with debug-specific parameter values.
Activity Output and Error Details
Each activity in a pipeline generates detailed logs that can be accessed via the Monitoring tab. These logs include:
Success Messages: Information about successfully completed activities.
Error Messages: Descriptions of failures, including error codes and stack traces.
Diagnostic Details: Data that helps identify the root cause of issues, making it easier to troubleshoot.
Retrying Failed Activities
ADF allows you to configure retry policies for activities. If an activity fails, it can automatically retry based on the configured retry count and interval, minimizing the need for manual intervention.
Data Preview Feature
While designing data flows, the Data Preview feature enables you to preview the transformed data before running the pipeline. This is especially useful for debugging data transformation issues or validating your mappings.
Integration with Azure Storage Logs
Since ADF often interacts with Azure Storage services, enabling diagnostic logging for your storage accounts allows you to:
Track data read/write operations.
Identify and resolve connectivity or authentication issues.
Best Practices for Monitoring and Debugging
To ensure smooth operations and prompt issue resolution, consider these best practices: Azure Data Engineer Training Online
Implement Logging: Leverage ADF’s built-in logging capabilities and integrate with Application Insights for comprehensive telemetry tracking.
Set Up Alerts: Configure alerts to monitor critical pipeline failure scenarios, such as exceeding SLA deadlines or experiencing operational delays.
Use Retry Policies: Enable retry logic to handle transient errors automatically, reducing the need for manual intervention.
Test Extensively in Debug Mode: Validate your pipelines thoroughly in Debug mode before deployment to ensure smooth execution.
Enable Diagnostic Logs: Turn on diagnostic logs for services like Azure Storage and SQL Database to assist with end-to-end troubleshooting.
Monitor Key Metrics: Use Azure Monitor dashboards to keep track of essential pipeline performance metrics, ensuring timely actions are taken when necessary.
Conclusion
Monitoring and debugging pipelines in Azure Data Factory are essential tasks for ensuring the efficiency, reliability, and performance of your data workflows. With ADF’s monitoring tools, Debug mode, and integration with Azure Monitor and Application Insights, you can proactively identify and resolve issues, minimizing disruptions and enhancing the performance of your data integration solutions. By adhering to best practices, such as implementing comprehensive logging, setting up alerts, and using retry policies, you can maintain optimal pipeline performance and quickly address any challenges that arise.
Visualpath is the Best Software Online Training Institute in Hyderabad. Avail complete Azure Data Engineering worldwide. You will get the best course at an affordable cost.
Attend Free Demo
Call on - +91-9989971070.
WhatsApp: https://www.whatsapp.com/catalog/919989971070/
Visit Blog: https://azuredataengineering2.blogspot.com/
Visit: https://www.visualpath.in/online-azure-data-engineer-course.html
#Azure Data Engineer Course#Azure Data Engineering Certification#Azure Data Engineer Training In Hyderabad#Azure Data Engineer Training#Azure Data Engineer Training Online#Azure Data Engineer Course Online#Azure Data Engineer Online Training#Microsoft Azure Data Engineer
0 notes